Losing your crypto to any kind of hack is devastating. It’s a day you will remember for a long… long time.
However, losing access to your Google Account as a result of a hack could totally ruin your life – and I’m not even exaggerating.
Protecting your Crypto means being protected everywhere.
If you use a Gmail account then you need to be aware of all of the potential risks.
Even if you are not using it directly for signing in to Crypto (we would strongly suggest you do not!) then you may not realize how much is collected that may make you (and your Crypto!) vulnerable if you should get hacked!
We have assembled the best information from Google Support, respected cyber-security websites, and authority articles on Google Security to help us develop a checklist of how to increase the security of a personal Google Account.
So why would a hacker even bother with your Google Account? What could they possibly find there that is worth something to them….?
What would Hackers find in your Google Account?
- Any website or organization where you have used this email for setting up the account is vulnerable!
- The Hacker simply goes to those companies clicks on the ‘Forgot Password’ and waits for the email to ‘Reset your Password’ to arrive in your hacked account! They can then lock you out of everything
- All the Banks, Credit Cards, Crypto Exchanges, Brokers & Crypto Wallets you use?
- All the Private and Valuable Emails you have sent to yourself with Sensitive information?
- Access to your Paypal, Amazon, Apple, Gambling, or Shopping sites?
- Access to your Social Media Accounts?
- Access to your YouTube Channel, Discord Server, Twitter Account, Telegram
- Access to all the Accounts where you have used this email as your recovery address?
- Access to your Domains & Websites.
- Private images that you definitely wouldn’t want sharing or could put you at risk of blackmail?
- Photos of passwords, mnemonics, or key phrases that would allow them to steal your crypto?
- Photos of personal ID such as your Passport, Driving License, Citizenship or Residence Card, or proof of address that would allow them to steal your identity and commit fraud?
- Screenshots of important information such as balances on Crypto Exchanges or Wallets that might lead the Hacker straight to your most precious assets
- Photos of just about anything that could expose you personally, professionally, or legally?
- Precious photo or video collections that you would be devastated to lose and don’t have backed up elsewhere?
- Work Documents & Files, Personal videos, Sensitive documents, and Master lists of Passwords?
- Mobile Phone Backups that could be used to clone your phone?
- Address books or lists of both Private or Professional Contacts that are now potential targets for the hacker?
- Ownership documents for your Car, Property, Boat, or Business?
- Personal or Business Accounts records?
- All the passwords you have saved in your Chrome browser to access your Crypto, Shopping, Entertainment, Gaming, Storage Accounts, Messaging, or Social Media accounts
- All the passwords and sites you use to be able to “work from home”?
- All your saved passwords via chrome://settings/passwords.
- All your Bookmarks that might provide clues to accounts the Hacker could target?
- All your Payment methods are via chrome://settings/payments.
- All your Home, Work, and previous Addresses via chrome://settings/addresses.
- All the sites you like to look at and the stuff you do online?
- Access to any sites where you have used the “Log in with Google” button?
- All your meetings, work schedules, private appointments, and whom you have been meeting with?
- Travel arrangements and holidays making you more vulnerable to attack?
- Contact details and Addresses
- The exact location of where you call Home, your Kids School, and your Family Addresses?
- Where you have been, how frequently, and when for the past 1-2 years?
- Where you are now?
(There are other apps within your Google account that we have not covered above that would also be vulnerable if your account was compromised!)
Locking down my Google Account.
Having discovered quite how much data Google was collecting about me and the implications should my account be hacked, I was in shock. All of this was available behind a single password that hadn’t been changed in several years!
Check to see if any of your passwords have been compromised:
https://haveibeenpwned.com/Passwords
NOTE: This is an independent website.
I stopped writing and spent more than half a day securing and locking down EVERYTHING!
I went through my Google Accounts to find out all the information it was recording about me that could be harmful in the wrong hands and deleted it or changed the settings so it stopped recording stuff.
I then ordered a hardware device for storing my passwords, turned on 2-factor authentication (2FA) and created an offline paper-based record of all my newly created login and recovery details.
Lastly, I looked into how easy the process was to restore my Google Account if it ever was hacked or compromised…I’ve got cherished photos/videos on there of my kids and I wouldn’t want to lose all my Gmail and Google Drive stuff.
Below are the twelve steps I followed to secure my Google Account.
Even if you do not have time to follow all these steps now, as a minimum check out at the end of this article what is required to ‘Recover your account if you are hacked‘.
It is NOT straight forward.
Securing Your Google Account
Step 1) Signing in to your Google Account
- Your Google Account needs to have an updated password that is strong and unique to this account. If you haven’t changed your password in the last 6 months or it’s a variation of other passwords you use elsewhere, change it now and record your new login details somewhere safe, offline ( Our Free Recording Sheet Printable), or use a secure password manager and authentication device.
To change your password, go to the Google Account Security page at https://myaccount.google.com/security.
- Go to your Google Account dashboard.
- In Chrome by clicking on ‘Manage your Google Account’ having clicked on your Account ID circle top right
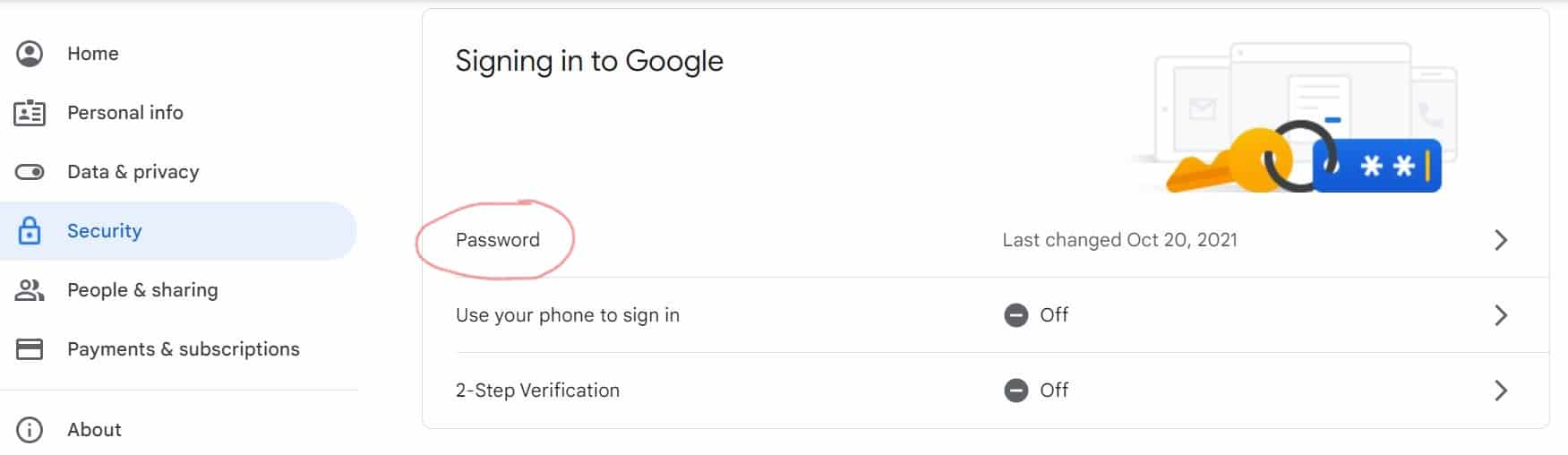
- On the left navigation panel, click Security.
- Scroll down to “Signing in to Google” click Password and follow the prompts to change your password.
If you are unsure whether the passwords you typically create are secure, click here to check out our article on secure passwords for suggestions on how to put together the most secure passwords.
This is what Google advises when it comes to passwords.
Create a strong password & a more secure account.
Step 2) 2-Step Verification
If you don’t already have 2-Step Verification or 2FA in place on your Google Account then a hacker only needs your password to access your entire Google Account, including YouTube, Gmail, Drive, Google Pay, and all the other Google apps you use.
If you have used your Google password anywhere else then you have created a single point of failure that is easy to exploit if your password gets discovered through a data breach elsewhere and is sold on to hackers.
2-step Verification adds another layer of security to your account and Google gives you a number of verification options to choose from. However, these options are not all equally secure.
Option 1: Receive a verification code on your phone by text (SMS) or call.
To sign into your account you will need your password and a unique 6-digit code that Google will send by SMS or phone call to a phone number you have previously shared. Every time you log in you will need to request a new code.
This option works ok until you don’t have mobile / cell signal, lose/damage/change your phone sim, the codes don’t arrive, you are the victim of Sim-Swapping, or your SMS is phished.
This is probably the least secure option on offer but is significantly more secure than just having a password login. Better to choose this than nothing at all! But you can do better!
Option 2: Use backup codes
You can choose to print or download a set of 8-digit backup codes from Google to use to login.
This option works well if you don’t wish to use a mobile device as part of your 2-step verification process, and if you don’t have access to your phone or you have no cell signal.
Option 3: Use Google Authenticator or another Authenticator App
Using an Authenticator App such as Google or Microsoft Authenticator on your cell phone allows you to receive one-time verification codes immediately without an internet connection or mobile service. New codes are generated every 30 seconds.
Google Authenticator is also available as a Chrome extension on Windows or Mac OS if you use a PC.
Option 4: Use a Hardware Security Key
A physical security key is a small USB/NFT/Bluetooth device that you can buy. You use it to complete 2-step verification when you sign in. You simply connect the security key to your phone, tablet, or computer to log in securely.
Adding 2-step Verification to your Google Account
- Go to your Manage Google Account dashboard
- On the left navigation panel, click Security.
- Scroll down to “Signing in to Google,” click “2-Step Verification and follow the onscreen guide.
Here are links to Google guides on 2-Step Verification that you may find helpful:
How to turn on 2-Step verification on Google`
Fix common issues with 2-Step Verification
Step 3) Google Account Recovery
Account Recovery Options
Google allows you to set up a Recovery Phone Number or Email Address to allow you to reset your password if you forget your password, someone else is using your account, or you are locked out of your account for another reason.
NOTE: These are not the same as recovering afterbeing hacked. If hacked all of these settings will be changed to stop you accessing your accounts!
Add a Recovery Phone Number and Email Address
- Go to your Google Account
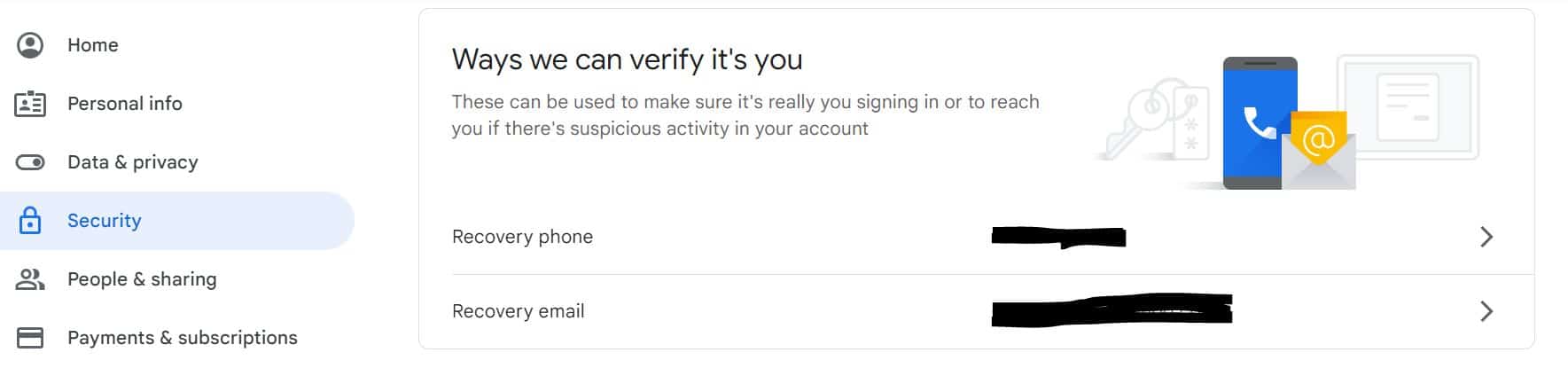
- On the left navigation panel, click Security.
- Scroll down to “Ways we can verify it’s you,”: Click Recovery email
- Follow the steps on the screen.
- Repeat for Recovery Phone
This is Google’s guide to setting up your Account Recovery:
Set up a recovery phone number or email address
Step4) Manage apps with access to your account
Google allows you to give permission to other non-Google apps to access your Google Account information. Examples of apps would include if you use an address book app or diary/calendar app that syncs with your Google Contacts or Calendar.
If you have not recently checked which apps have this permission then here is a process to check for yourself and delete any permissions for apps you no longer use or don’t trust.
How to Review / Remove App access to your Google Account
- Go to your Manage Google Account dashboard
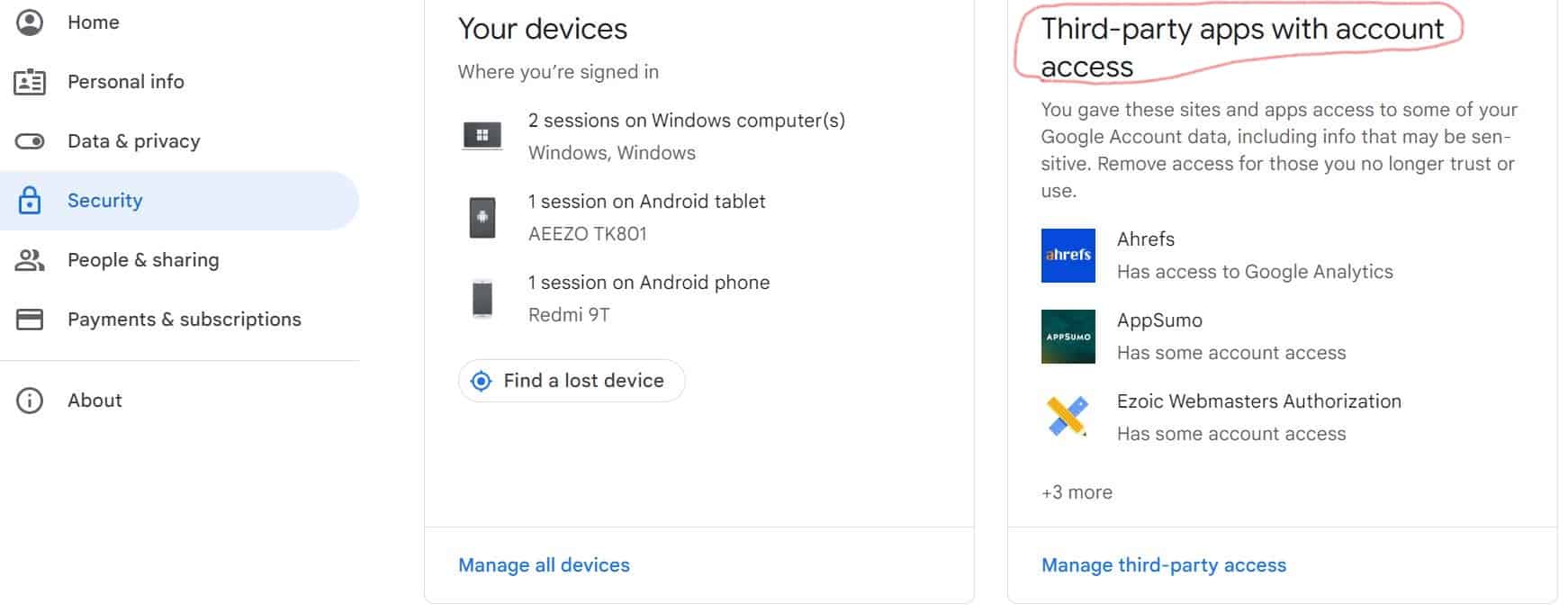
- On the left navigation panel, click Security.
- Scroll down to “Third-party apps with account access,” select Manage third-party access.
- Select the app or service you want to Review or Remove.
This is Google’s guide to Managing 3rd Party Apps:
Manage third-party apps & services with access to your account
Step 5) Update your software
It is very important to keep your PC and Mobile Device software up to date to ensure you have the latest software releases and security patches. You may have updates set up automatically but it is worth checking.
- Keeping your operating system updated is one of the most important steps in protecting yourself from viruses, malware, and other security threats.
- Keeping your Anti-virus / Malware / Firewall/ VPN software updated is also essential to ensure you are protected from the latest threats.
If you are just getting into Crypto and don’t already have solid Antivirus/Malware protection on your devices, this should be made a priority.
- You need to be extra careful in choosing which software to use, but most importantly where you download it from.
- Don’t download anything from anywhere other than the main software developer’s website.
- Never be tempted by “hacked versions” of expensive security software that someone is sharing for free out of the goodness of their heart!
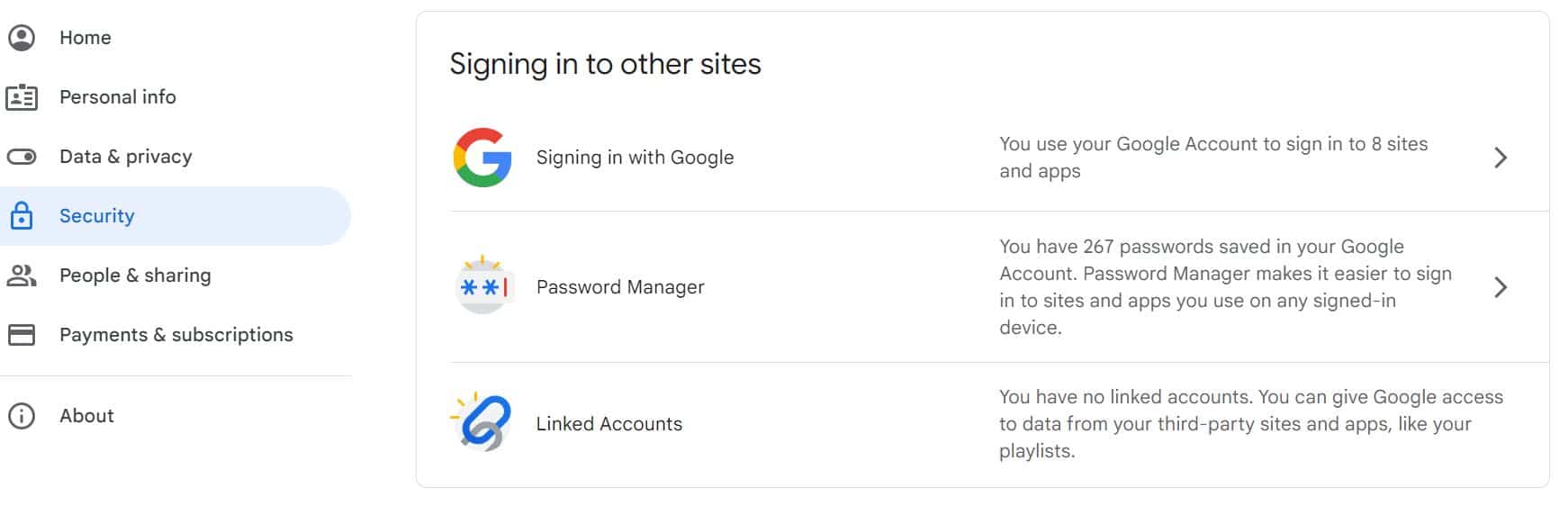
Step 6) Using your Google Account to sign in to 3rd party Apps
Some apps and websites such as Social Media, Online Shopping, and Music Streaming allow you to connect or log in with your Google Account or install 3rd party extensions on your browser to make it quicker and easier for you to access their websites.
Whilst this is very convenient it is also a significant security risk if your Google Account is subsequently compromised. A hacker would potentially have access to every account you use your Google login with.
If you are not absolutely sure which apps you are logging into with your Google Account you can follow this process to find out and manage permissions. If you no longer want to use your Google Account to sign in to a third-party app or service, you can remove access.
How to Manage 3rd-Party Accounts
- Sign in to your Google account
- Select Security and scroll down to “Signing in to other sites” and choose Signing in with Google.
- Choose the app or service you want to review or remove and then follow the steps..
Here is a link to Google Support that walks you through managing your Google Sign-ins:
Use your Google Account to sign in to other apps or services
Step 7) Manage the Data that your Google Records about you!
I had genuinely given little thought to the types and amount of data that Google records about me, and what I do until I began researching this article.
It is possible to review this data, delete what you don’t want Google to keep, and change how or if this data is recorded in the future.
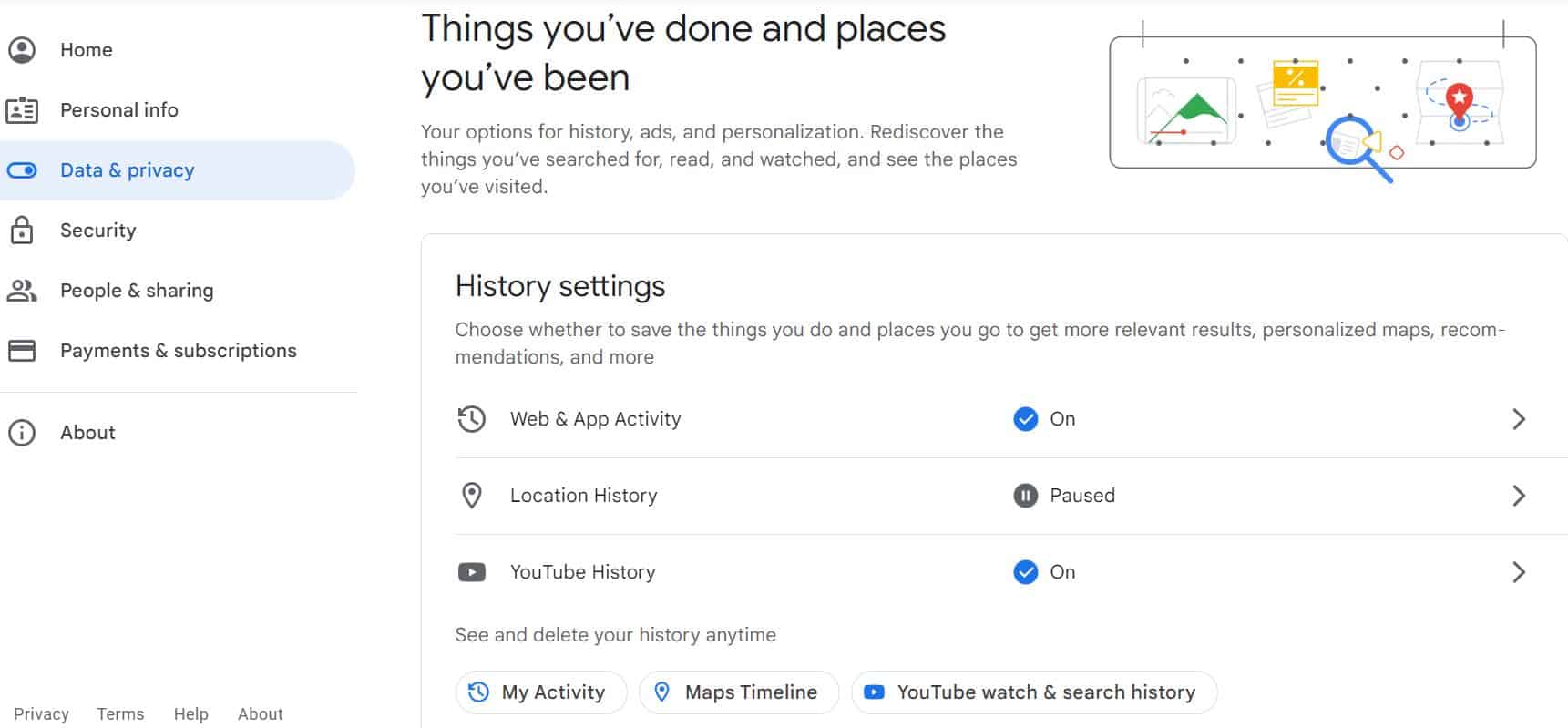
How to Check Data that Google Records about you:
- Login to your Google Account
- Select Data & Privacy and scroll down to History Settings,
- You are able to change your settings for your Location History, Web & App activity, and YouTube History
How to Manage your Location History
If you have Google location enabled on your cell phone/PC, and take it with you when you go out, your Google Timeline will show on a map everywhere you’ve been, how frequently, and for how long.
This can be handy if you want to verify for yourself where you were on a particular date, but otherwise, it is basically a digital tracker that publishes this data into your Google Account!!

I wouldn’t choose to take a personal tracking device with me everywhere I go so the first thing I did was change the settings on my Location History!
How to Change Settings for Location History
- Within your Google Account and Select Data & Privacy
- Scroll down to Location History (as explained above) to manage settings and the data that is already recorded about you in your account:
Manage your Web & App Activity records
If Web & App Activity is turned on you will see a record of EVERYTHING you have searched for and done using Google and connected Apps saved in your Google Account.
You can manage these settings on an app by app basis and also choose to delete data already held on your account.
Find & control your Web & App Activity
Step 8) Manage the Devices that have access to your Google Account
How to Check which devices are accessing your Google Account
- Go to your Manage Google Account dashboard
- On the left navigation panel, click Security.
- Scroll down to “Your Devices”
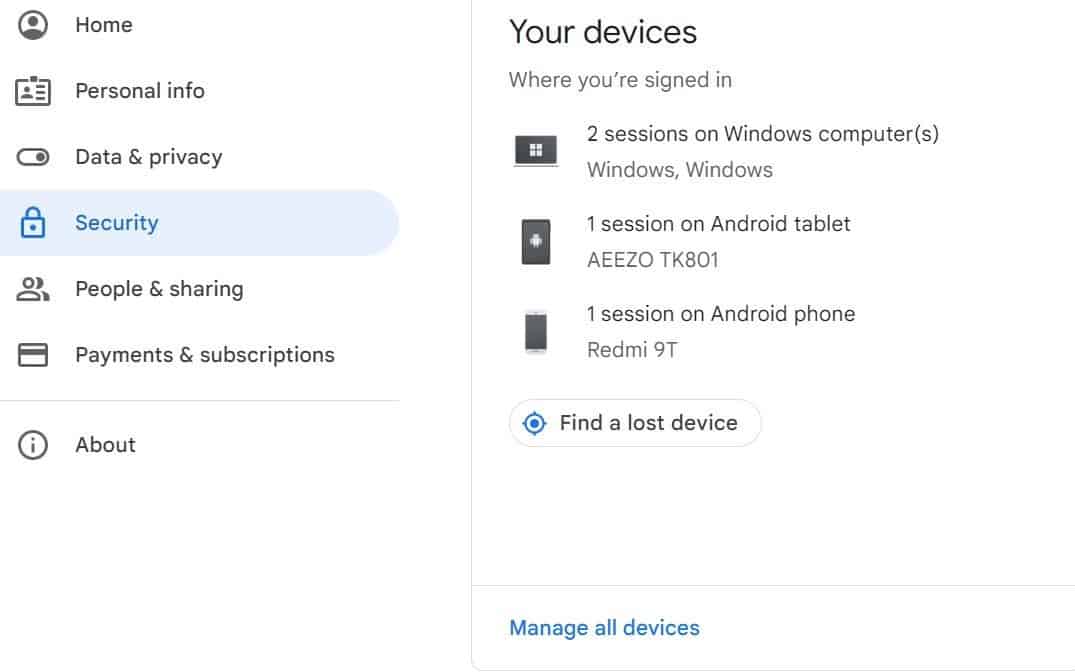
Your Google account keeps a record of all the computers, phones and devices where you are currently signed into your Google Account or where you have previously signed in.
It is worth checking this Device list regularly to:
- make sure you aren’t still logged in on a device that is not your main PC or mobile device.
- Remove permissions from devices if they are no longer relevant (e.g Ex-partners devices, friends devices that you have borrowed or devices you have sold or lost)
- Identify if an unknown device has access to your account.
This feature is handy if your PC or phone is lost or stolen as you can log in to your Google account from another device and remove phone access to your account. You can also see if someone else is logged into and using your account!
Step 9) Manage your Gmail
“
If a hacker were to get access to your Google Account they could seriously “own you” if you have your “eggs all in one Google basket”!
“
If you are using the same Gmail Address to login to your Banks, Credit Cards, Crypto Exchanges, Brokers, Crypto Wallets, Paypal, Amazon, Apple, Gambling, Shopping sites, or Social Media Accounts etc etc…
… it is time to immediately upgrade your personal online security.
To do this you are going to need to:
- Create several new Encrypted Email Addresses, (See our article for guidance)
- With unique and secure passwords (See our article for guidance)
- With 2 Factor Authentication enabled, preferably using an Authenticator App or Hardware Device.
- Record all your new email addresses/logins offline somewhere secure (link to recording sheet) or use a trusted password manager like LastPass or 1Pass together with an authentication device.
Avoid using a Gmail account as your Recovery Email
If you are using your main Gmail account as the Backup/Recovery address for any of your Crypto/Financial/Social media/Shopping accounts, should a hacker get access to your recovery email address it means they could lock you out of all related accounts by changing the login details.
If you are using one Gmail address as the Backup/Recovery address for another Google account this is also something you are going to want to change.
- Choose an alternative email provider to set up your recovery email address.
- Only use this email address ONLY for Account Recovery purposes (rather than for signing-up to apps and services etc)
- Decide whether it is beneficial to make this the Recovery Email Address for other accounts you hold?
If you are using your main Gmail account to login to your Domains/Websites/Social Media Channels/Online Shops it would be wise to create a new encrypted email address secured with 2FA dedicated solely to each Website or Channel and not use this email address anywhere else.
If you are using your main Gmail Account to save Private and Valuable Emails or Sensitive information you should start off by asking yourself why?
Does this need to be stored as an email in a Google Account?
Could you move it somewhere safer such as a hardware device, or through an app/software specifically designed to store private data?
If you need to store it in an email account maybe set up a dedicated email account for this purpose?
Step 10) Secure your Internet Browser
If you are using Google Chrome as your Internet Browser you may want to seriously consider exploring other secure browsing options if you plan to visit or interact with any Crypto Apps, Wallets, Exchanges or Websites. Chrome rarely appears in Top 10 Reviews of Secure Internet Browsers…. Go check for yourself!
Unless properly configured your Internet Browser contains lots of private information about you that could be collected or exploited by third-party companies as well as hackers.
This includes:
- Your Browsing History, Searches, and all the websites you visit
- Login credentials, Usernames, and Passwords
- Cookies and Trackers
- Autofill information such as your Name, Address, Date of Birth, Phone numbers etc.
There are additional layers of privacy and security you can add to increase your online protection which we will talk you through below, but there is one key thing you should understand….
Unless you are using a VPN:
EVERYTHING you do online can be tracked and recorded by anyone motivated to do so.
“Private” or “Incognito” browsing modes do not hide your I.P Address or location and all your search activity is recorded by your Internet Service Provider(ISP).
If you check the small print of your Agreement with your ISP you will probably discover you have agreed to them sharing your data with any 3rd-parties they deem fit.
A good VPN is critical for basic digital privacy, especially if you are in Crypto!
It is as critical as having a Hardware wallet!
As an example, we use the free Proton VPN combined with the Brave Browser.
Okay, so lets talk you through how to lock down your Google Chrome Browser.
Google Chrome offers 3 safety features called Privacy Guide, Safety Check, and Privacy & Security which cover Site Settings, Cookies, Browsing Data, Compromised passwords, Safe browsing status, available Chrome updates, harmful browser extensions and harmful software (Windows only).
How to Secure your Chrome Browser
- Open the Chrome Browser
- Click on the three dots “More” button in the top tool bar
- Choose Settings and then Privacy & Security from the drop down box
- This will bring you to a page that shows you the Privacy Guide, Safety Check and Privacy & Security settings.
- For the Privacy Guide, select “Get Started” and follow the steps
- For the Safety Check, select “Check Now”
- For the Privacy & Security settings, select each heading one by one to review and change your settings.
Step 11) Google Photos
Google can and does access your photos stored in Google Photos!
You agree to it as part of your free storage deal.
This is also true for any other App you have given permission to use your camera.
(TikTok, Instagram, Facebook etc)
This doesn’t just mean the pictures of you eating ice cream. It’s also the documents you photographed for proof of address, passport application, scans of bank details, hotel bookings when you are away, Crypto Passphrase, etc, etc.
All are easily and instantly read, using AI text recognition software.
Nice and private then?
The sort of place where you would want to store sensitive photos or videos?
Google does offer an option to hide sensitive photos and videos but this is only available on Android 6 or later.
Here is a link to Google’s Locked Folder set-up process, there are some drawbacks to it but it may be an improvement on what you already have in place.
However, if you are likely to take or wish to store private or sensitive photos you should be looking at a more secure option than Google Photos!
The other thing to consider is how valuable certain photos are to you?
If your cell phone is backing up everything to Google Photos then you will have a mix of pics you want to keep, photos that are precious and random pics that backed-up before you had chance to delete them.
Our advice would be to back-up those precious photos somewhere else, either through another cloud photo provider or by downloading them to an external storage device.
Step 12) Check for suspicious activity
If Google notices suspicious activity in your account they’ll send you a notification. It may be that there are sign-ins from an unfamiliar location or an unfamiliar device.
To review your account security it is much safer to login to your Google Account directly rather than clicking on any link in an email as this is one of the ways hackers can trick you into being re-directed to a fake website that will steal your login details.
Check your Gmail Account filters for forwarding emails It’s important that you ensure that there are no active filters in your account which may be forwarding your email to a third-party email address.
This check is simple:
- Go to your Gmail Settings page and click on the Filters tab.
- Look for filters you haven’t authorized or don’t use and delete them.
Googles Advanced Protection Program
Google currently offers a free Advanced Protection Program that safeguards Google Account users with high visibility and sensitive information from targeted online attacks.
It requires you to have at least one 2FA hardware device, though recommends 2 so you have a backup.
If you use crypto and have a hardware device to store your private keys then having a hardware device for your online security is a no-brainer! They are also much cheaper than Hardware wallets.
Now that you’ve secured your Google Account, take a few more minutes to lock down your Amazon account. Then, do the same for your Social Media, Banking & Payment Accounts while you’re at it.
Recovering your Google Account following a Hack.
“
It is not as straightforward as you might think to recover your Google account if it gets hacked and taken over.
“
This is not the same as forgetting your password!
There doesn’t appear to be a customer services number you can call or a human to talk to.
You are at the mercy of a Fully Automated AI-style Account Recovery Process.
You are required to answer a series of questions to verify you are the owner of the Google Account. If you don’t have the answers ready, your account could be suspended!
Here are the key bits of information you need to record somewhere safe, just in case you ever need to recover your Google Account:
- Any phone numbers linked to the account
- Recovery phone number or email address that you have set up.
- Your most recent password and previous passwords you have used for the account
- Backup Codes that you have requested and printed off
- The names of the devices you usually use to login to your account
- The different locations you usually use when you login to your account.
- 3rd Party Apps that are linked to your Google Account.
We found two helpful guides that offer step-by-step advice/tips on how to recover your Google Account.
How to Recover your Google Account
Tips to Complete Account Recovery
Conclusion
If you have made it this far well done!
Google offers some really valuable free features that all work together in one place – you barely have to think about it as Google does it for you.… But it makes money by selling your data, snoops on everything you do, and leaves a record of it on your account.
If you don’t nail security on each aspect of your account then you could be in big trouble if someone does hack their way in.
Remember a hack doesn’t mean you have been personally targeted. It could simply involve somebody buying thousands of leaked password details on the dark web and systematically going thru them to find out who has poor security.
Don’t let it be you!
We are interested to hear about the experiences of crypto users who have had their Google Account compromised.
Please leave a comment below and we will gladly get back in touch.
